kubernetes的ingress配置多个tls证书 |
您所在的位置:网站首页 › kubernetes ingress tls › kubernetes的ingress配置多个tls证书 |
kubernetes的ingress配置多个tls证书
|
背景需求:
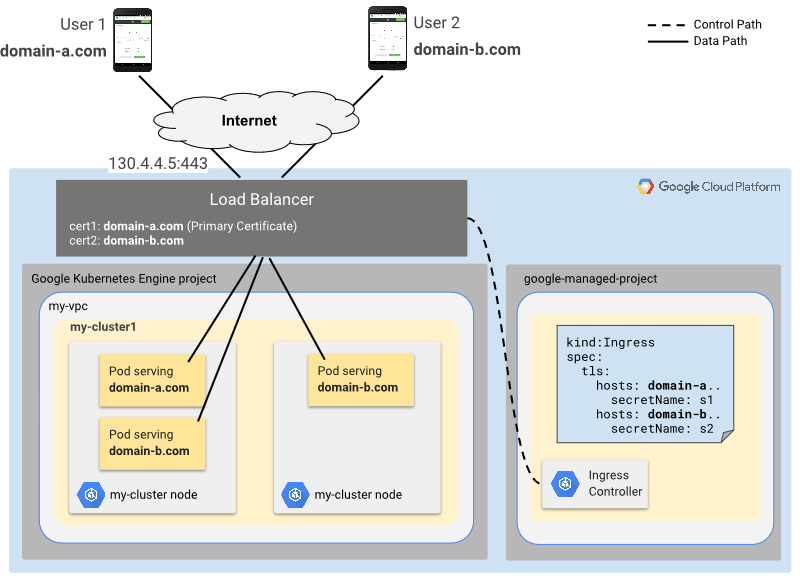
有多个域名,且每个域名走HTTPS 示例架构:
测试环境: 公有云提供Kubernetes环境,自动创建负载均衡IP 示例步骤: 1. 创建一个Deployment 2. 创建一个Service 3. 创建2个证书和2个密钥文件 4. 创建使用Secret和Ingress 5. 测试HTTPS(负载均衡IP) 具体配置: 1. 准备一个Deployment文件 my-mc-deployment.yaml   apiVersion: apps/v1
kind: Deployment
metadata:
name: my-mc-deployment
spec:
selector:
matchLabels:
app: products
department: sales
replicas: 3
template:
metadata:
labels:
app: products
department: sales
spec:
containers:
- name: hello
image: "gcr.io/google-samples/hello-app:2.0"
env:
- name: "PORT"
value: "50001"
- name: hello-again
image: "gcr.io/google-samples/node-hello:1.0"
env:
- name: "PORT"
value: "50002"
View Code
apiVersion: apps/v1
kind: Deployment
metadata:
name: my-mc-deployment
spec:
selector:
matchLabels:
app: products
department: sales
replicas: 3
template:
metadata:
labels:
app: products
department: sales
spec:
containers:
- name: hello
image: "gcr.io/google-samples/hello-app:2.0"
env:
- name: "PORT"
value: "50001"
- name: hello-again
image: "gcr.io/google-samples/node-hello:1.0"
env:
- name: "PORT"
value: "50002"
View Code
应用此Deployment: kubectl apply -f my-mc-deployment.yaml
2. 准备一个Service文件 my-mc-service.yaml   apiVersion: v1
kind: Service
metadata:
name: my-mc-service
spec:
type: NodePort
selector:
app: products
department: sales
ports:
- name: my-first-port
protocol: TCP
port: 60001
targetPort: 50001
- name: my-second-port
protocol: TCP
port: 60002
targetPort: 50002
View Code
apiVersion: v1
kind: Service
metadata:
name: my-mc-service
spec:
type: NodePort
selector:
app: products
department: sales
ports:
- name: my-first-port
protocol: TCP
port: 60001
targetPort: 50001
- name: my-second-port
protocol: TCP
port: 60002
targetPort: 50002
View Code
应用此Service文件: kubectl apply -f my-mc-service.yaml
3. 创建证书和密钥(这里以两个域名为例) 说明:两个证书,每个证书都有一个相应的密钥,每个证书的公用名 (CN) 必须与您拥有的域名一致。 创建第一个密钥: openssl genrsa -out test-ingress-1.key 2048创建第一个证书签名请求(其中,first-domain 是您拥有的域名或虚构域名): openssl req -new -key test-ingress-1.key -out test-ingress-1.csr -subj "/CN=first-domain"创建第一个证书: openssl x509 -req -days 365 -in test-ingress-1.csr -signkey test-ingress-1.key -out test-ingress-1.crt创建第二个密钥: openssl genrsa -out test-ingress-2.key 2048创建第二个证书签名请求(其中,second-domain 是您拥有的另一个域名或虚构域名): openssl req -new -key test-ingress-2.key -out test-ingress-2.csr -subj "/CN=second-domain"创建第二个证书: openssl x509 -req -days 365 -in test-ingress-2.csr -signkey test-ingress-2.key -out test-ingress-2.crt
4. 创建Secret和Ingress 创建包含第一个证书和密钥的Secret: kubectl create secret tls first-secret-name --cert first-cert-file --key first-key-file创建包含第二个证书和密钥的 Secret: kubectl create secret tls second-secret-name --cert second-cert-file --key second-key-file创建Ingress文件 my-mc-ingress.yaml apiVersion: networking.k8s.io/v1beta1 kind: Ingress metadata: name: my-mc-ingress spec: tls: - hosts: - first-domain secretName: first-secret-name - hosts: - second-domain secretName: second-secret-name rules: - host: first-domain http: paths: - backend: serviceName: my-mc-service servicePort: my-first-port - host: second-domain http: paths: - backend: serviceName: my-mc-service servicePort: my-second-port应用该Ingress文件: kubectl apply -f my-mc-ingress.yaml 根据不同的云厂商,稍等一会(分配负载均衡的外网IP),可以查看一下Ingress: kubectl describe ingress my-mc-ingress   Name: my-mc-ingress
Address: 203.0.113.1
...
TLS:
first-secret-name terminates
second-secret-name terminates
Rules:
Host Path Backends
---- ---- --------
your-store.example
my-mc-service:my-first-port ()
your-experimental-store.example
my-mc-service:my-second-port ()
Annotations:
...
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal ADD 3m loadbalancer-controller default/my-mc-ingress
Normal CREATE 2m loadbalancer-controller ip: 201.0.113.1
View Code
Name: my-mc-ingress
Address: 203.0.113.1
...
TLS:
first-secret-name terminates
second-secret-name terminates
Rules:
Host Path Backends
---- ---- --------
your-store.example
my-mc-service:my-first-port ()
your-experimental-store.example
my-mc-service:my-second-port ()
Annotations:
...
Events:
Type Reason Age From Message
---- ------ ---- ---- -------
Normal ADD 3m loadbalancer-controller default/my-mc-ingress
Normal CREATE 2m loadbalancer-controller ip: 201.0.113.1
View Code
5. 测试HTTPs 要执行此步骤,您需要拥有两个域名,并且两个域名都必须解析 HTTP(S) 负载平衡器的外部 IP 地址 curl -v https://first-domain ... * Trying 203.0.113.1... ... * Connected to your-store.example (203.0.113.1) port 443 (#0) ... * TLSv1.2 (IN), TLS handshake, Certificate (11): ... * Server certificate: * subject: CN=your-store.example ... > Host: your-store.example ... ; Hello, world! Version: 2.0.0 ... curl -v https://second-domain ... * Trying 203.0.113.1... ... * Connected to your-experimental-store.example (203.0.113.1) port 443 (#0) ... * Server certificate: * subject: CN=your-experimental-store.example ... > Host: your-experimental-store.example ... Hello Kubernetes!
结束 |
【本文地址】